News from trendmicro.
Our researchers at TrendLabs have discovered a new set of rogue antivirus software circulating in the wild. Based on initial analysis, these threats arrive mainly via spammed email messages that contain a link to a bogus celebrity video scandal. We have also received reports that the said link is circulating in instant messaging applications and private messages in social networking Web sites, too.
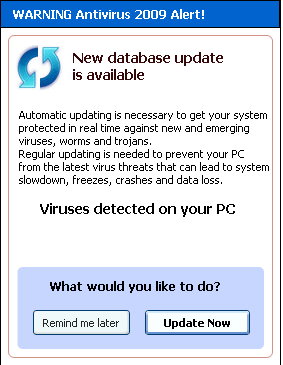
Once the said URL link is clicked, the Web threat infection chain begins and ultimately leads to the download of a Trojan detected by Trend Micro as TROJ_FAKEAV.CX. This Trojan is a rogue antivirus that displays very convincing (and
for some, alarming) messages, such as the following:
TROJ_FAKEAV.CX also drops another malware, detected as TROJ_RENOS.ACG. RENOS Trojans are known to have very visual payloads that may further alarm users — for example, they modify the system’s wallpaper and screensaver settings to display BSOD (Blue Screen of Death/Doom). Thus, users may be more convinced that something’s wrong with their system, not knowing that their new software is the one causing it.
Rogue antispyware isn’t entirely new, although our researchers have been seeing an increase in activity for the past couple of months (the Anjelina spam being one of the more recent examples).
Perhaps it’s because this is also the time of the year when the more legitimate security suites are releasing their latest software updates, and cyber criminals are riding on this season to ramp up their profits. Bad news for the infected users, though, as their latest versions of “antivirus software” are actually adding more threats to their system.
Trend Micro is still investigating this spam run. Updates will be posted when more information becomes available.